
Unchecked addition of best_bid_price and best_ask_price when saving mid price can cause a global auction pause for all traders as an attacker can place one very high-price ask and one small-price bid so both best prices exist; then mid_price = (bid + ask) / 2 overflows and the auction submessage fails, which sets PAUSED = true.
In cron.rs:630 the mid price is computed by adding both prices then halving:
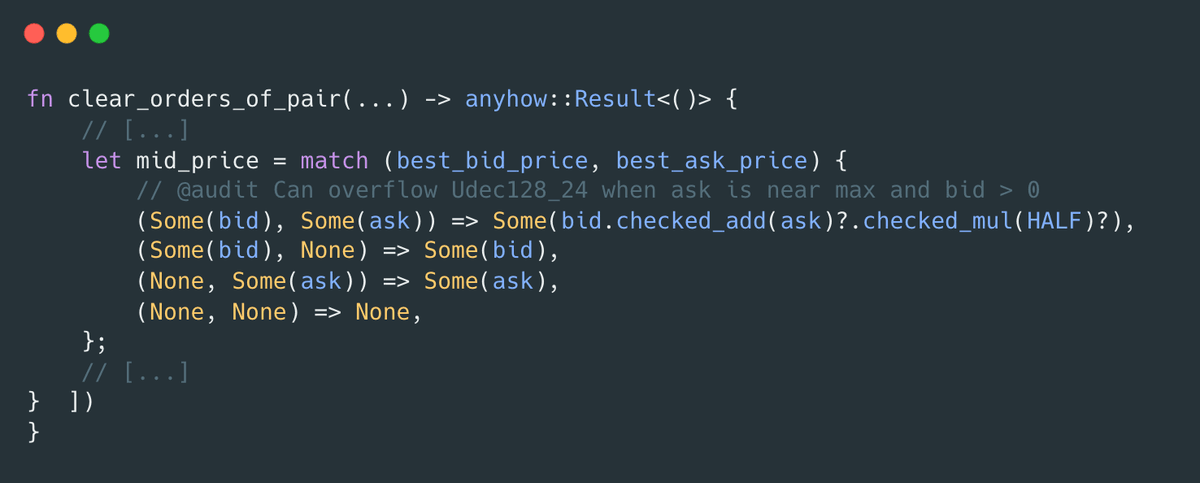
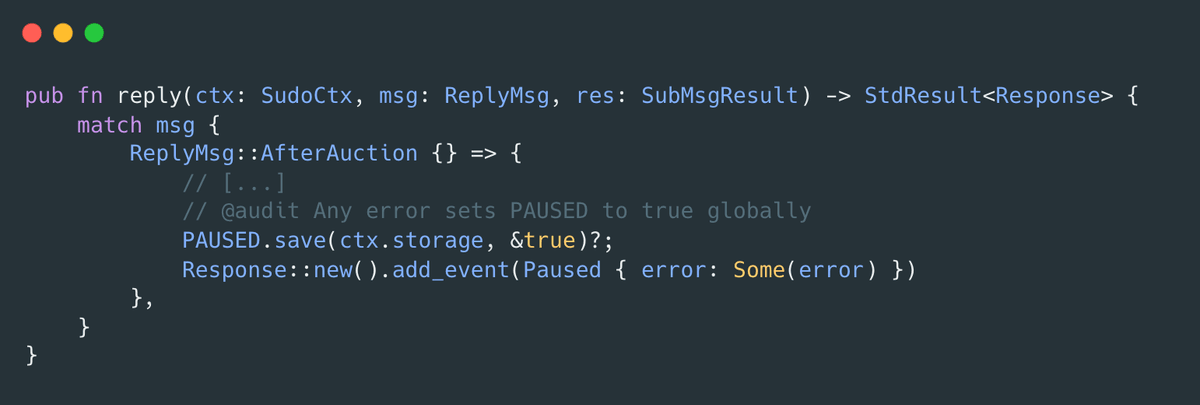
Adding two Price (Udec128_24) numbers can overflow when ask is near the max and bid is positive. The error bubbles up, the auction submessage fails, and the reply handler pauses trading in cron.rs:65:
Note: There is a very important condition needed, the pair must not have passive pool reserves yet, so no passive orders cap prices; best bid/ask come only from user orders. This is extremely important to mention, otherwise it may get invalidated.
Attack Path
1. Attacker sends a GTC SELL (ask) with extreme price (A) close to Price max (Udec128_24).
2. Attacker sends a GTC BUY (bid) with small price (e.g., 1) and quote >= min_order_size (e.g., $10).
3. No match happens (1 < A), so at end of block, the contract saves resting book.
4. It computes mid_price = Some(bid.checked_add(ask)?.checked_mul(HALF)?).
5. bid + ask overflows Udec128_24, so the submessage errors and the reply handler sets PAUSED = true.
Alpha: always check all the math equations for over/underflow, downcasting, rounding.
Conclusion
This finding would earn you $3318, and can be come up essentially by adding to your check list that all math operations must be checked for correct behaviour. Addition, make sure to spend enough time understanding all of the conditions and the correct impact, so it doesn't get invalidated.
Full Report
Codebase