Although this finding doesn't pay exceptionally well, there are 24 dups, but it contains a key information about Uniswap v4.
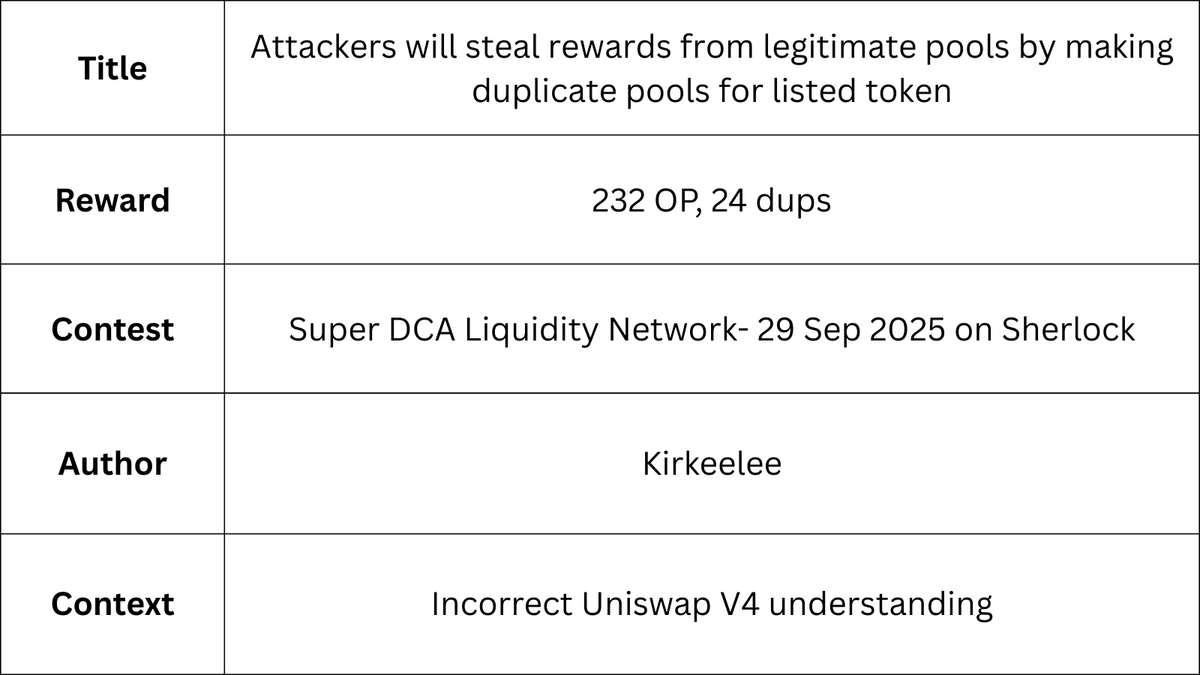
The Uniswap v4 pool configuration, as opposed to v3, allows the creation of any number of pools with the same token pair, but the protocol was not aware of this. The pool key, which identify each pool, is different for the following parameters:
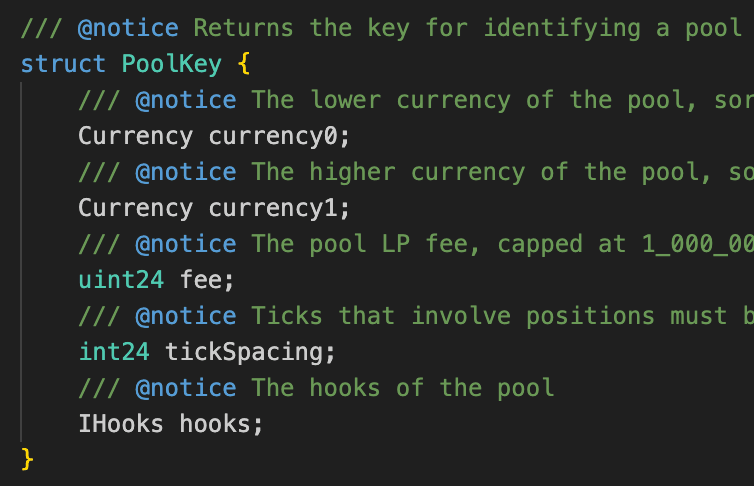
More about Uniswap v4 hooks, here. Key functionality, modify liquidity hooks, called when adding or removing liquidity (even if 0).
Weaponizing it
1. Attacker identifies a listed token (e.g., USDC) with an existing legitimate pool (e.g., USDC/SuperDCA with dynamic fee).
2. Attacker creates a new malicious pool for the same pair (USDC/SuperDCA) using the same SuperDCAGauge hook, with minimal or zero liquidity (bypassing listing requirements).
3. Attacker adds minimal liquidity to the malicious pool, triggering _beforeAddLiquidity which calls _handleDistributionAndSettlement.
4. In _handleDistributionAndSettlement, rewards are accrued for the token (USDC) globally, and the community share is donated to the malicious pool (since it has liquidity).
5. Attacker removes liquidity from the malicious pool, triggering _beforeRemoveLiquidity again, potentially accruing more rewards.
6. Attacker repeats add/remove operations to maximize reward theft, then withdraws the donated rewards from the malicious pool.
Conclusion
This finding would earn you 232 OP, so as per the OP price at the time you can probably afford a fancy dinner.
